Running a business website without assuring its security is like risking your entire empire. In recent times, it’s not a new thing to hear a popular website being hacked, and the data is stolen. According to a survey report, 2020 has been an unsafe year for companies across the globe. Statistics suggest that there have been increased website hacking cases since the COVID-19 outbreak, as many organizations chose to remain functional by creating their online business realm.
However, not paying attention to cyber threats gave criminals and access to spy, intrude, and finally, hack major business websites. And as reasons may vary, the common thing noticed was these websites lack proper security solutions. And now when a new survey was made in 2020’s second quarter, it is observed that 73% of businesses, freelancers, and digital agencies are worried about their website preservation.
So, whether you have a huge eCommerce set up, or a small informational website that explains your services, you should get it guarded with a Web Vulnerability Scanner (WVS), as well as, Web Application Firewall (WAF) to shield your business from all the corners.
Curious to know what WVS and WAF are and how they can help you strengthen your business. We’ve got everything for you here. So, dive in!
What is a Web Vulnerability Scanner?
A Web Vulnerability Scanner is a software that is programmed to automatically scan web applications and websites to reveal any hidden security issues and vulnerabilities within them, which could be extremely damaging for the business. Undeniably, it’s a boon for all organizations, as it allows them to quickly find the weaknesses in the site. Plus, WVS is simple to use that even people with minimum computer knowledge can handle it.
Securing Your Website with Web Vulnerability Scanner – Best Way to Identify Threats
So now you know the main reason for WVS’s inception. Let’s unearth what threats this software can identify.
1. Cross-Site Scripting
Cross-site scripting, also called the XSS, is a type of vulnerability where the attacker gets access to a host website by injecting malicious JavaScript codes.
With the help of this vulnerability, the hacker enjoys stealing cookies, exploiting all browser vulnerabilities, and intruding on calling application features by using another person’s identity.
The most common example could be cross-site scripting the business website by sending malicious script through contact or search forms. The threat cannot be identified without a WVS, as it comes from the usual ways, just like a client or a customer sending queries by visiting your site’s contact form.
2. SQL Injection
In SQL injection, the attacker can have complete unauthorized access to all the data available in your website’s database. In this type of threat, attackers can extract all the information including clients’ or company’s usernames, passwords, and other confidential data.
What happens is that the attackers get to the back-end of your database and copy, modify, or delete all the database contents. Moreover, attackers can also modify cookies to damage the database query.
3. OS Command Injection
OS Command Injection is made to execute arbitrary commands on a targeted operating system. And unfortunately, vulnerable websites become the main channel that allows attackers to infect the data with ease.
And as a result, the attack could lead to Denial of Service, and Remote Code Execution. Also, this well-known vulnerability gives complete control to the attackers on your application, and they are free to manipulate, delete, or disclose any sensitive information from the database.
4. Insecure Communication
Your server communicates with the web browser through HTTP protocol. This helps transfer unencrypted data and information over the network. But when your website has several vulnerabilities, attackers use them to cease and cut off the communication right from the network.
And not just that, but they are even able to modify or amend the transmitted data including credit card information, secret tokens, passwords, and many more. In all cases the modified data is undetectable, and only a powerful WVS can help you secure the communication.
5. Server Information Disclosure
This attack is intending to acquire unique or particular information about any website. Attackers can use different files to search all backend application details, server software, and even their versions.
Also, with this attack, they can identify names of the directories, their structure, and contents through a robots.txt directory. Then, the source code files allow them access to temporary backups.
6. Interesting File Found
The Interesting File Found is a common web vulnerability that uses folders or files with some certain sensitive data to help cyber criminals prepare further attacks against the website server. However, manual validation is necessary for this crime.
7. Missing HTTP Security Headers
HTTP security headers are the basic part of your website’s security. Once they are implemented, they protect the site against several attacks, such as code injection, clickjacking, XXS, and many more.
So imagine what would happen if the headers go missing? Well, that’s what attackers can do when it comes to stealing the information. Therefore, a WVS is much-needed to assure none of your HTTP is missing, no matter what tricks attackers plan on the users.
The above information is to help you understand the importance of a WVS. Now, let’s find out what a Web Application Firewall is all about, how sweet are its fruits to your business?
What is a Web Application Firewall?
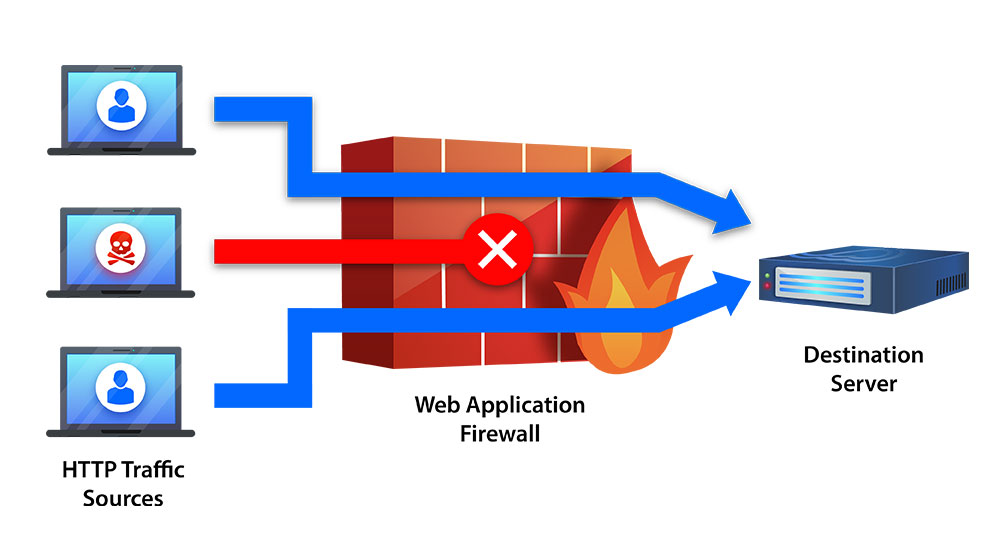
WAF works using the reverse-proxy concept, where a user, who is trying to visit your website, is not directly exposed to the server. Instead, he or she has to pass through a Web Application Firewall to determine whether or not the user is safe to enter the site.
With WAF, you can expect protection from multiple attacks, such as cross-site scripting and cross-site forgery, but more robustly and effectively due to a 7-layered defense protocol.
Web Application Firewall is functional through a ‘set of rules’, which are normally considered as ‘policies’. They secure websites against numerous vulnerabilities by screening malicious traffic.
Reasons Why Implementing Web Application Firewall is an Intelligent Decision
Wondering why WAF could be a great deal for your business operations? The following reasons can surely help you get the answers.
1. Safeguarding
Websites with insufficient cybersecurity prevention methods are often the soft targets of the attackers. Contrarily, WAFs main work is to secure such websites from any unauthorized data exposure. They are quite crucial for businesses, which are functional through the internet, especially online retailers, and eCommerce platforms. WAF allows such businesses to store their private information and user data with complete protection.
2. Scanning Vulnerabilities for Temporary Fix
Let’s take an example of the eCommerce industry. As COVID-19 is still present among us, many businesses are now being operational online. Considering that, let’s divide them into two groups. The first group is a huge eCommerce business with hundreds of staff and adequate IT resources. The second group is of small individual eCommerce businesses, though pretty much financially stable and have lots of customers, but don’t have resources to tackle attacks.
The first group is likely to cover the loss and recover the data, as it is equipped with professionals in the IT department, which are expected to take down any threat by hook or crook. On the other hand, small eCommerce ventures are easy to intrude on, and their data is at high risk. And if they are being attacked there are minimum chances of their survival.
However, both groups are at 100% risks of getting damaged when the attacks are made by expert attackers, who would use different tricks to obtain what they desire. And the gateway would be the website. So in such critical scenarios, WAF plays a key role in stopping attacks by scanning vulnerabilities and fixing them as soon as they are identified. And despite the fix is temporary, it does give time to business owners to think of permanent solutions to ensure prevention.
3. Ceasing Data Leakage
Hackers have numerous ways to steal data. And mostly, there won’t be any sign of being struck until you hear the news, but by that time, it would be already late. Why? Because the data will be leaked from an internal source.
Data leakage is one of the ways to attack a website. Regardless of attackers’ intentions, it is very common in the corporate world.
So, if your website and includes some extremely significant user data, such as credit card or social security numbers, there could be someone ready to do the inside job.
But the best part is that when you have WAF, any attempt to leak the data will soon be identified and blocked. The firewall is developed in a way that scans each request, made by any user when it leaves your network.
4. Monitoring Web Traffic
A Web Application Firewall secures web applications by monitoring and filtering the HTTP traffic between the internet and website. So when your business site is live, a WAF can recognize any unusual activity or intervention coming from the internet, and filter it out immediately.
5. Protection from DDoS and Brute Force Attacks
Last but not the least, WAF protects your website from downtime caused by the DDoS. Additionally, the software prevents trial-and-error attacks, also called, a brute force attack, where hackers try to trespass on your website by entering all possible encryption keys (passwords) to get access.
Conclusion
Relying on your website without securing it from attackers could be way too risky. There are many prying eyes, waiting to find vulnerabilities in your site to capture confidential information. Therefore, it is important to take all the necessary measures to obstruct hackers from destroying the reputation you have created with your blood and sweat.
One of the best ways to secure your website is to use WVS and WAF. And to make things smooth and effortless, Net Onboard offers the best Web Vulnerability Scanner and Web Application Firewall solutions to minimize vulnerability and savor sanctuary against imperceptible threats.
Curious to know more details about our WVS and WAF services? Drop us an email regarding your enquiry and requirement and we are glad to assist you!























