The Malice of the Internet – Computer Virus
Computer Virus, you have probably heard about it, feared about it, and you most probably have encountered it at least once. You probably have been prompted to get the best Anti-Virus to repel attacks. But do you know what you are facing up against?
There are many different kinds of computer viruses, ranging from worms, trojan horses, ransomware and so forth. Each of them attacks you differently, leaving your system crippled.
To effectively fight an enemy, you must first understand your enemy. This is one of the most important secrets to winning a battle. So, in conjunction with the up and coming Computer Security Day, which will be on the 30th of November, I shall break down the details of a few famous viruses in a little virus history crash course.
Be mindful that this is made to be as simple as possible for those who have zero knowledge about computer viruses.
Creeper
This made the list not because it was the most potent, or the most famous. I added this in as an honorary mention because this is the first virus ever.
Ironically, given the reputation of computer viruses, Creeper is virtually harmless. All that it does is display a message on your screen that says ‘I’m the creeper, catch me if you can!’.
It all started in 1970 when Bob Thomas decided he wanted to do something mischievous. His masterpiece was spread from BBN Technologies’ DEC PDP-10 through Arpanet. It was named Creeper, a name which he took inspiration from a character in Scooby-Doo.
This also triggered the first Anti-Virus program to ever be made. It was developed with the sole purpose of deleting Creeper. It was appropriately named The Reaper.
Loveletter
During the year 2000, one of the biggest worm outbreaks ever occurred. It is also the first billion-dollar outbreak in history. This one outbreak is speculated to have caused damages of around $87.5 Billion. More than 45 million computers across the globe have been infected by it.
Written by Onel A. de Guzman, a computer student in the Philippines, the Loveletter virus was injected via an email. The email would typically have a subject line of ‘ILOVEYOU’ together with an attachment name ‘LOVE-LETTER-FOR-YOU.TXT.vbs’, hence the name ‘Loveletter’.
This worm will rewrite and modify files on your PC. It will also prompt your computer to download a trojan that will send information about your PC to an email located in the Philippines. Then it will proceed to send itself to any emails that are in the contact book of infected PCs.
Infamously, this worm is known for causing a major Denial-Of-Service (DOS) breakdown of the official white house webpage.
Storm Worm
The Storm Worm outbreak started during late 2006, it is dubbed by some as the most disastrous virus outbreak ever. The program is a Trojan Horse, meaning it passes itself as a legit executable file, but in truth, it contains something malicious inside it.
Storm Worm comes in the form of an email, usually with a title such as ‘230 dead as storm batters Europe’. This is how the virus got its name. Attached to the email is a link which contains the trojan horse.
Once infected, Storm Worm will open a backdoor towards your computer, turning your computer into a BotNet. This can be used by attackers at a later time to inflict damage without the consent of the owner.
An estimated 200 million emails containing the virus was sent during the period of the outbreak. Even though not every single one of them was opened.
Although this outbreak happened on an enormous scale, it is not hard to counter. Not long after the outbreak, most Anti-Virus applications are already updated to detect and remove this virus.
MyDoom
First discovered during 2004, MyDoom is a worm program that spreads itself by sending copies through infected computers to other emails. It was known as the fastest-spreading worm at that time.
Mydoom targets a backdoor Port 3127 on unpatched versions of Window’s system. It was designed to attack SCO’s website, who had an issue at that time with the Linux Community regarding copyrights of some open-source software.
The issue got so out of hand that SCO group offered a whopping $250,000 as a reward to anyone who managed to catch the culprit behind the attacks.
Not long after, a new version of the virus named MyDoom.B was found. It was intended to attack Microsoft instead. Following suit of SCO, Microsoft also put a $250,000 bounty on the head of the virus maker.
The author of MyDoom is unknown, many speculate that it was a Russian who was behind this.
During the peak of its invasion, MyDoom caused web speeds to be slowed by 50%, with every 1 in 12 of all emails containing the worm.
CryptoLocker
CryptoLocker is a Trojan Horse that encrypts your files. To have your files decrypted, you have to pay a ransom fee to an unknown account. Then you will get the key to unlocking your files. This is known as ransomware.
Again, like most viruses, it comes in the form of an email. In the email is a link with two extensions. One fake, such as .pdf or .html and the real one behind it. Once it penetrates your system, it will encrypt all files connected to your devices, including USBs that are inserted into your PC.
To obtain the key to unlock it, there will be a ransom amount shown on your screen. If you failed to pay before the deadline, all your files will be deleted. The ransom amount differs between different devices.
In 2014, government agencies and internet security companies alike join forces to launch ‘Operation Tovar’. Its goal is to shut down the Gameover ZeuS botnet, which is believed to have been used in the distribution of the CryptoLocker Virus.
The operation was a success, not only did they managed to cut off the Botnet, they also managed to track it back to Evgeniy Bogachev, otherwise known as ‘lucky12345’. He is believed to be the mastermind behind CryptoLocker.
Bogachev and his gang has extorted around $3million by using this ransomware.
Protect yourself
Hopefully, all this data would help you understand viruses better than before. This is essential for preventing them from ever reaching your computer.
As many examples above have shown, remember to never trust emails with unknown sources. It will save you from a lot of hassle later on.
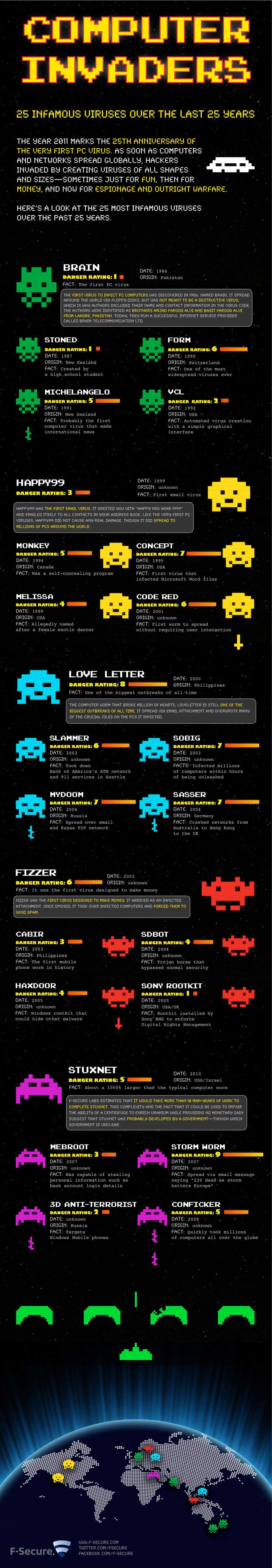
If you want to know more, take some time to appreciate this tidy infographic made by F-Secure. It details some of the most important viruses to have appeared in our history. Do give it a look.
From all of us at Net Onboard, Happy Computer Security Day!























